 There is a relatively active virus on the loose called CryptoWall 3.0. People experienced problems with this virus in recent days. The virus attacks .jpg, Office and other files and encrypts them so they’re unable to be opened. Unfortunately, the virus is also considered “ransomware” which means the author attempts to extort users into paying to get the encrypted files unlocked. Reports indicate that the initial ransom starts at $500.00 and the files may remain unavailable even after paying the fee.
There is a relatively active virus on the loose called CryptoWall 3.0. People experienced problems with this virus in recent days. The virus attacks .jpg, Office and other files and encrypts them so they’re unable to be opened. Unfortunately, the virus is also considered “ransomware” which means the author attempts to extort users into paying to get the encrypted files unlocked. Reports indicate that the initial ransom starts at $500.00 and the files may remain unavailable even after paying the fee.
My experience shows that multiple anti-virus programs have been unsuccessful at blocking this attack. We’ve also had mixed results when attempting to restore files from backups.
It appears that the virus is primarily being transmitted via normal methods: email attachments and embedded links within emailed documents. As always, be sure you know your sender before opening any attachments and, if uncertain about the message, contact the sender before opening the suspect email. If in doubt, delete the suspect email message. Several users have downloaded .zip, .pdf and .jpg files, plus other file extensions with .exe names. Unfortunately, this is quite common since organizations are reviewing job applicant credentials and are processing orders/tracking shipments: Both of these message types may include file attachments.
The virus has encrypted files on local hard drives, external drives (like backup systems) as well as flash drives and shared network locations. Again, there is no guarantee that we can restore files once they’ve been encrypted.
Once your computer has been infected we’ve see several hints:
1) Your Internet Explorer and/or Chrome browser home pages will be redirected to the Ransomware site.
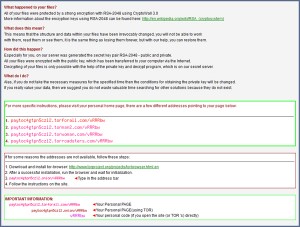
2) Files with the following names will begin to appear in folders, on the desktop, on the network:
– help_decrypt.txt
– help_decrypt.png
– help_decrypt.html
IF you see any of these files or if your browser home page is hijacked to a different location than normal, immediately shut down the computer in order to reduce the risk of further file corruption, then contact me.
Finally, I would not be a bad idea to have several flash drives in use as alternative backup options. Backup any critical files and keep rotating them every three days or so in case the last backup is already corrupted. Unfortunately, if the virus is already on your system then the backups files could be corrupted and useless.